I run Debian 10 on a MacMini3,1 as a home router for various reasons.
I have an iMac G4 with an AirPort card which supports WEP but not WPA.
A WEP network is so insecure that it’s effectively open
and I don't want to be running netatalk, smb, mssql etc. on
an open network. MAC address filtering (in hostapd and in iptables)
is not considered secure —
although WEP and MAC address would probably be good enough here in Shropshire.
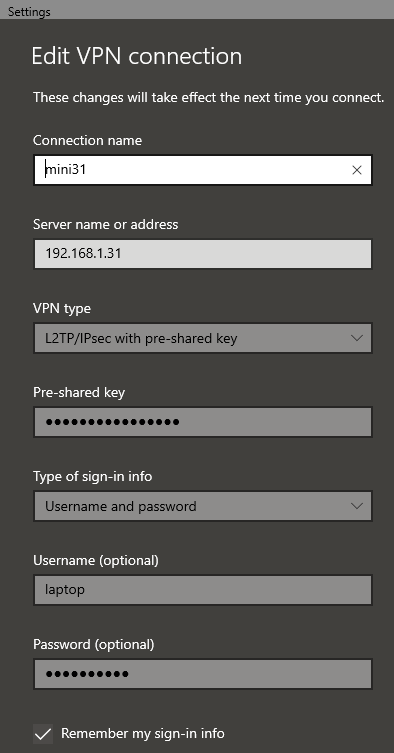
I notice that the Mac OS X 10.3 Internet Connect application includes an option for IPSec/L2TP and this could provide a solution. The WEP AP is on a separate subnet (192.18.2.0/24) so all ports except for IPSec and L2TP can be closed. That means that anything on the WEP network:
So: how to set it up?
# apt-get install strongswan # apt-get install libcharon-extra-plugins # Seems to have the things in /etc/strongswan.d/charon. Or maybe libstrongswan or libstrongswan-standard-plugins? # apt-get install xl2tpd # apt-get install ppp
/etc/ipsec.conf
config setup
conn wep-ap
type=transport
authby=secret
pfs=no
rekey=no
keyingtries=1
left=%any
leftid=%any
right=%any
auto=add
esp=aes128-sha1-modp1536
ike=aes128-sha1-modp1536
include /var/lib/strongswan/ipsec.conf.inc
/etc/strongswan.conf
charon {
plugins {
include strongswan.d/charon/*.conf
eap_dynamic {
preferred = eap-mschapv2, eap-tls
}
}
}
The include thing seems to be important, and that the direcotry exists and has files in it.
/etc/ipsec.secrets
%any %any : PSK "password"
/etc/ppp/chap-secrets
laptop * password *
/etc/ppp/options.xl2tpd
noccp auth mtu 1410 mru 1410 nodefaultroute proxyarp silent debug ms-dns 192.168.3.31
/etc/xl2tpd/xl2tpd.conf
[global] ; Global parameters: port = 1701 ; ** Bind to port 1701 access control = no [lns default] ; Our fallthrough LNS definition ip range = 192.168.3.100-192.168.3.254 ; ** But this one is okay local ip = 192.168.3.31 ; ** Our local IP to use name = mini31 ; ** Report this as our hostname pppoptfile = /etc/ppp/options.xl2tpd
In Windows:

And in `syslog`:
mini31 # cat -n syslog | tail +3203
3203 Nov 20 20:24:45 mini31 charon: 13[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (408 bytes)
3204 Nov 20 20:24:45 mini31 charon: 13[ENC] parsed ID_PROT request 0 [ SA V V V V V V V V ]
3205 Nov 20 20:24:45 mini31 charon: 13[ENC] received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:01
3206 Nov 20 20:24:45 mini31 charon: 13[IKE] received MS NT5 ISAKMPOAKLEY vendor ID
3207 Nov 20 20:24:45 mini31 charon: 13[IKE] received NAT-T (RFC 3947) vendor ID
3208 Nov 20 20:24:45 mini31 charon: 13[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
3209 Nov 20 20:24:45 mini31 charon: 13[IKE] received FRAGMENTATION vendor ID
3210 Nov 20 20:24:45 mini31 charon: 13[ENC] received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
3211 Nov 20 20:24:45 mini31 charon: 13[ENC] received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
3212 Nov 20 20:24:45 mini31 charon: 13[ENC] received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
3213 Nov 20 20:24:45 mini31 charon: 13[IKE] 192.168.1.11 is initiating a Main Mode IKE_SA
3214 Nov 20 20:24:45 mini31 charon: 13[CFG] selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384
3215 Nov 20 20:24:45 mini31 charon: 13[ENC] generating ID_PROT response 0 [ SA V V V V ]
3216 Nov 20 20:24:45 mini31 charon: 13[NET] sending packet: from 192.168.1.31[500] to 192.168.1.11[500] (160 bytes)
3217 Nov 20 20:24:45 mini31 charon: 14[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (228 bytes)
3218 Nov 20 20:24:45 mini31 charon: 14[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
3219 Nov 20 20:24:45 mini31 charon: 14[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
3220 Nov 20 20:24:45 mini31 charon: 14[NET] sending packet: from 192.168.1.31[500] to 192.168.1.11[500] (212 bytes)
3221 Nov 20 20:24:45 mini31 charon: 15[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (76 bytes)
3222 Nov 20 20:24:45 mini31 charon: 15[ENC] parsed ID_PROT request 0 [ ID HASH ]
3223 Nov 20 20:24:45 mini31 charon: 15[CFG] looking for pre-shared key peer configs matching 192.168.1.31...192.168.1.11[192.168.1.11]
3224 Nov 20 20:24:45 mini31 charon: 15[CFG] selected peer config "wep-ap"
3225 Nov 20 20:24:45 mini31 charon: 15[IKE] IKE_SA wep-ap[6] established between 192.168.1.31[192.168.1.31]...192.168.1.11[192.168.1.11]
3226 Nov 20 20:24:45 mini31 charon: 15[ENC] generating ID_PROT response 0 [ ID HASH ]
3227 Nov 20 20:24:45 mini31 charon: 15[NET] sending packet: from 192.168.1.31[500] to 192.168.1.11[500] (76 bytes)
3228 Nov 20 20:24:45 mini31 charon: 06[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (316 bytes)
3229 Nov 20 20:24:45 mini31 charon: 06[ENC] parsed QUICK_MODE request 1 [ HASH SA No ID ID ]
3230 Nov 20 20:24:45 mini31 charon: 06[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
3231 Nov 20 20:24:45 mini31 charon: 06[IKE] received 3600s lifetime, configured 0s
3232 Nov 20 20:24:45 mini31 charon: 06[IKE] received 250000000 lifebytes, configured 0
3233 Nov 20 20:24:45 mini31 charon: 06[ENC] generating QUICK_MODE response 1 [ HASH SA No ID ID ]
3234 Nov 20 20:24:45 mini31 charon: 06[NET] sending packet: from 192.168.1.31[500] to 192.168.1.11[500] (188 bytes)
3235 Nov 20 20:24:45 mini31 charon: 05[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (60 bytes)
3236 Nov 20 20:24:45 mini31 charon: 05[ENC] parsed QUICK_MODE request 1 [ HASH ]
3237 Nov 20 20:24:45 mini31 charon: 05[IKE] CHILD_SA wep-ap{6} established with SPIs c2b5d044_i 1726a3e2_o and TS 192.168.1.31/32[udp/l2f] === 192.168.1.11/32[udp/l2f]
3238 Nov 20 20:24:46 mini31 xl2tpd[12817]: control_finish: Peer requested tunnel 3 twice, ignoring second one.
3239 Nov 20 20:24:48 mini31 xl2tpd[12817]: control_finish: Peer requested tunnel 3 twice, ignoring second one.
3240 Nov 20 20:24:52 mini31 xl2tpd[12817]: control_finish: Peer requested tunnel 3 twice, ignoring second one.
3241 Nov 20 20:25:00 mini31 xl2tpd[12817]: control_finish: Peer requested tunnel 3 twice, ignoring second one.
3242 Nov 20 20:25:10 mini31 xl2tpd[12817]: control_finish: Peer requested tunnel 3 twice, ignoring second one.
3243 Nov 20 20:25:16 mini31 xl2tpd[12817]: Maximum retries exceeded for tunnel 13486. Closing.
3244 Nov 20 20:25:16 mini31 xl2tpd[12817]: Connection 3 closed to 192.168.1.11, port 1701 (Timeout)
3245 Nov 20 20:25:20 mini31 charon: 09[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (76 bytes)
3246 Nov 20 20:25:20 mini31 charon: 09[ENC] parsed INFORMATIONAL_V1 request 3379181600 [ HASH D ]
3247 Nov 20 20:25:20 mini31 charon: 09[IKE] received DELETE for ESP CHILD_SA with SPI 1726a3e2
3248 Nov 20 20:25:20 mini31 charon: 09[IKE] closing CHILD_SA wep-ap{6} with SPIs c2b5d044_i (696 bytes) 1726a3e2_o (0 bytes) and TS 192.168.1.31/32[udp/l2f] === 192.168.1.11/32[udp/l2f]
3249 Nov 20 20:25:20 mini31 charon: 10[NET] received packet: from 192.168.1.11[500] to 192.168.1.31[500] (92 bytes)
3250 Nov 20 20:25:20 mini31 charon: 10[ENC] parsed INFORMATIONAL_V1 request 309590672 [ HASH D ]
3251 Nov 20 20:25:20 mini31 charon: 10[IKE] received DELETE for IKE_SA wep-ap[6]
3252 Nov 20 20:25:20 mini31 charon: 10[IKE] deleting IKE_SA wep-ap[6] between 192.168.1.31[192.168.1.31]...192.168.1.11[192.168.1.11]
mini31 #
My interpretetation is that IPSec connects successfully but that L2TP fails on line 3243 and I can’t work out why.
I was wrong: when starting up ipsec was producing error messages about missing plugins.
mini31 # systemctl status ipsec ? strongswan.service - strongSwan IPsec IKEv1/IKEv2 daemon using ipsec.conf Loaded: loaded (/lib/systemd/system/strongswan.service; enabled; vendor preset: enabled) Active: inactive (dead) since Mon 2022-08-08 11:20:37 BST; 13s ago Process: 21360 ExecStart=/usr/sbin/ipsec start --nofork (code=exited, status=0/SUCCESS) Main PID: 21360 (code=exited, status=0/SUCCESS) Aug 08 11:20:37 mini31 systemd[1]: strongswan.service: Succeeded. Aug 08 11:20:37 mini31 ipsec[21360]: charon has quit: initialization failed Aug 08 11:20:37 mini31 ipsec[21360]: charon refused to be started Aug 08 11:20:37 mini31 ipsec[21360]: ipsec starter stopped Aug 08 11:20:37 mini31 charon[21374]: 00[LIB] feature CUSTOM:libcharon-sa-managers in critical plugin 'charon' has unmet Aug 08 11:20:37 mini31 charon[21374]: 00[LIB] failed to load 3 critical plugin features Aug 08 11:20:37 mini31 charon[21374]: 00[DMN] initialization failed - aborting charon Aug 08 11:20:37 mini31 ipsec_starter[21360]: charon has quit: initialization failed Aug 08 11:20:37 mini31 ipsec_starter[21360]: charon refused to be started Aug 08 11:20:37 mini31 ipsec_starter[21360]: ipsec starter stopped
The directory /etc/strongswan.d/charon was empty.
An identical configuration to that described above worked on a RasberryPi but /etc/strongswan.d/charon
had lots of files in it.
So I copied those files to Debian and that made it work!